Let’s break down the process of creating a secure VPC environment using Terraform on AWS. Here’s a comprehensive step-by-step guide, explanations, and code examples to get you started.
Project : Create Secure VPC Environment
- Requirement: Create a foundational, secure Virtual Private Cloud (VPC) for your AWS deployments.
- Quick Summary:
- Defines the VPC’s CIDR block.
- Creates public and private subnets across multiple Availability Zones.
- Implements Internet Gateways and NAT Gateways for connectivity.
- Establishes security groups to control network traffic.
Prerequisites
- AWS Account: Ensure you have an active AWS account. If not, create one.
- Terraform Installation: Download and install Terraform on your local system from https://www.terraform.io/downloads.html.
- AWS CLI: Install and configure the AWS Command Line Interface (CLI) to interact with AWS from your terminal. Instructions: https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-install.html
- Text Editor/IDE: You’ll need a text editor or IDE (like Visual Studio Code) to write Terraform code.
Step to Follow:
Step 1: Project Setup
- Create a Directory: Make a new directory to organize your project files. For example:

- File Creation: Inside the directory, create a file named
main.tf. This is where your Terraform configuration will reside.

Step 2: Provider Configuration
AWS Provider: Open your main.tf file and start by adding the AWS provider block. This tells Terraform you’ll be working with AWS resources.
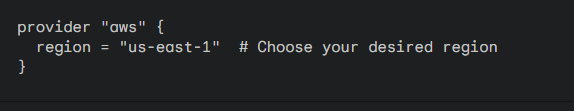
Step 3: VPC Creation
VPC Definition: Let’s define the main VPC resource:
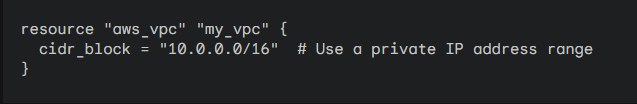
Note: Your file will look like as below:
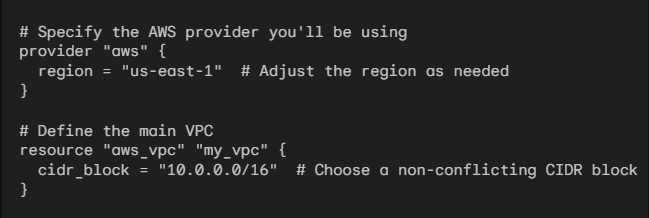
Step 4: Create Subnets
Add Subnet Definitions: Expand your main.tf file to create public and private subnets within the VPC:

Step 5: Internet Connectivity
Internet Access: Establish an Internet Gateway to connect your VPC to the internet:
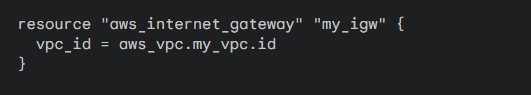
Step 6: NAT Gateway (for private subnets)
Outbound Connectivity: Create NAT Gateways for private subnets to reach the internet without exposing private IP addresses.

Step 7: Route Tables
- Routing Configuration: Define route tables to control traffic:

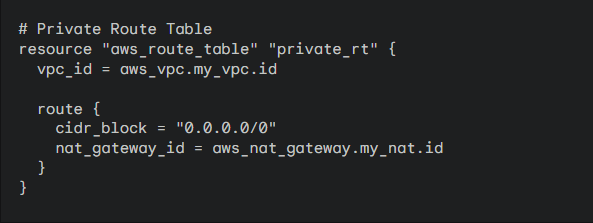
2. Private Route Table: Create a route table for the private subnets:
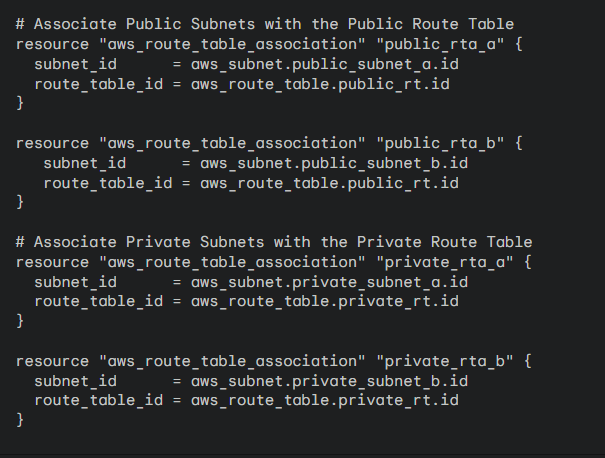
3. Subnet Associations: Associate subnets with their respective route tables:
Step 8: Security Groups
Define Security Groups: Create security groups to act as network firewalls:

Step 7: Apply the Configuration
1. Review: Go over your main.tf file carefully.
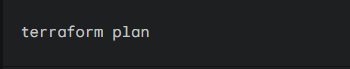
2. Plan: Execute the plan command to see what Terraform will create:
3. Apply: Finally, run the apply command to deploy the resources to your AWS account:
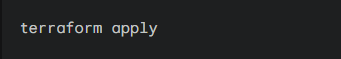
Type yes when prompted to confirm your changes.
Important Considerations
- Security Best Practices: Tighten security groups further. Instead of
0.0.0.0/0, restrict access to the specific IP ranges required. - Customization: Modify CIDR blocks, subnet divisions, and other settings to suit your specific needs.
- Additional Resources: In a production environment, you would add resources like EC2 instances, databases, load balancers, etc., within this secure VPC structure.
Terraform Project 1 – Solution (step by step)
Terraform : 5 Mini Projects to get Hands-on
Kubernetes : 5 Mini Projects to start with
Prometheus and Grafana (5 bite size Projects)
Hope you find this post helpful.
Telegram: https://t.me/LearnDevOpsForFree
Twitter: https://twitter.com/techyoutbe
Youtube: https://www.youtube.com/@T3Ptech