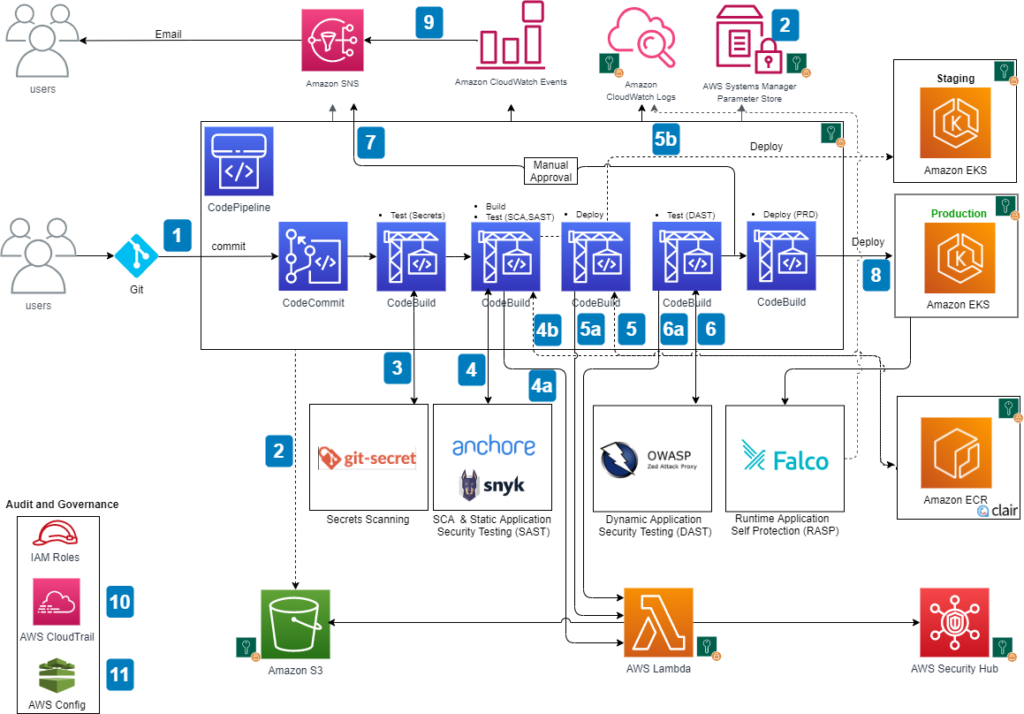
1. Commit Code:
- A developer commits code changes to a version control system like CodeCommit.
2. CodePipeline Triggered
- This triggers a CloudWatch event, which initiates the CodePipeline.
3. CodeBuild Performs Build and Uploads Artifacts
- CodeBuild, a service that builds, tests, and deploys code, takes the committed code, builds it, and uploads the artifacts (executable files) to an Amazon S3 bucket (storage).
4. CodeBuild Scans for Secrets
- CodeBuild scans the code for any sensitive information like passwords or API keys using a tool like git-secrets.
If it finds any, the build fails. This ensures secrets are not accidentally stored in the code.
5. CodeBuild Scans for Vulnerabilities (SCA & SAST)
- CodeBuild creates a container image from the code and scans it for vulnerabilities using Snyk or Anchore. These tools identify vulnerabilities in the open-source libraries used within the code.
6a. Remediation for Vulnerabilities Found (SCA & SAST)
- If vulnerabilities are found, CodeBuild invokes a Lambda function. This function translates the findings into a standard format (ASFF) and sends them to Security Hub, a central repository for security findings. Security Hub helps you view all findings in one place. The Lambda function also uploads the scan results to an S3 bucket.
6b. Push Image to ECR and Scan Again (ECR built-in)
- If there are no vulnerabilities (from step 5), CodeBuild pushes the container image to Amazon ECR, a container image registry.
ECR then scans the image for vulnerabilities using its built-in scanning feature.
7a. Remediation for Vulnerabilities Found (ECR Scan)
- If vulnerabilities are found by ECR, the Lambda function (mentioned in step 6a) is invoked again. It processes the findings and sends them to Security Hub and an S3 bucket.
7b. Deploy to Staging Environment (EKS)
- If no vulnerabilities are found (from step 7a), CodeBuild deploys the container image to a staging environment in Amazon EKS (Elastic Kubernetes Service), a managed Kubernetes service.
8. DAST Scan (OWASP ZAP)
- After successful deployment to staging, CodeBuild performs Dynamic Application Security Testing (DAST) using the OWASP ZAP tool. This tool identifies vulnerabilities in the running application by simulating real-world attacks.
9a. Remediation for Vulnerabilities Found (DAST)
- If DAST finds vulnerabilities, the Lambda function (mentioned in step 6a) is invoked again to process the findings and send them to Security Hub and an S3 bucket.
9b. Approval Stage and Production Deployment
- If no vulnerabilities are found (from step 9a), an approval stage is triggered. An email notification is sent via Amazon SNS (Simple Notification Service) to someone (e.g., security team) for approval to deploy the code to production.
Once approved, CodeBuild deploys the application to the production Amazon EKS environment.
10. Monitoring and Logging
- Throughout the pipeline, CloudWatch Events monitors the build and sends notifications to subscribed users.
- CloudTrail tracks API calls and sends notifications about critical events.
- AWS Config tracks configuration changes of AWS services and enforces security best practices.
Complete Post to Implement:
Free Courses : Microsoft Azure (Concepts + Hands-on)
Free Courses : Kubernetes (Enroll Now)
EKS for Simplified Kubernetes (AWS)