- Q.26 What are Kubernetes resource quotas, and how do they impact cluster management?
- Q.27 How can you secure communication between Kubernetes components?
- Q.28 What is a Kubernetes ConfigMap, and how do you use it?
- Q.29 Discuss the benefits of using Helm for managing Kubernetes applications.
- Q.30 How do you monitor and visualize Kubernetes cluster health?
Q.26 What are Kubernetes resource quotas, and how do they impact cluster management?
Kubernetes resource quotas are mechanisms that allow you to set limits on the amount of computational resources (CPU, memory) and object counts (pods, services) that can be consumed by a namespace. This helps ensure fair resource distribution and prevents applications from monopolizing the cluster.
Use Cases:
- Preventing Resource Exhaustion: Quotas stop rogue applications from consuming excessive resources and starving other workloads.
- Capacity Planning: They aid in anticipating and allocating resources effectively.
- Cost Control (Multi-tenant): In shared environments, quotas can be used to limit resource usage by teams or projects, helping manage costs.
Example:
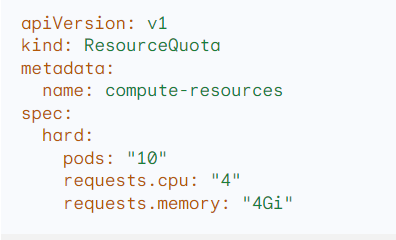
Q.27 How can you secure communication between Kubernetes components?
Securing Kubernetes communication involves multiple layers:
- Network Policies: Use Network Policies to define fine-grained rules for allowing or denying traffic flows between pods.
- TLS Encryption: Enable TLS encryption for communication between all Kubernetes components (kubelet, API server, etcd) using certificates.
- RBAC (Role-Based Access Control): Implement RBAC to enforce the principle of least privilege, limiting users and service accounts to only necessary permissions.
- Secrets Management: Use a Secrets manager (e.g., Kubernetes Secrets, Vault) to store sensitive information instead of plain text in configuration files.
Use Cases:
- Preventing Unauthorized Access: Securing communication channels and enforcing access control protects against data breaches and misuse.
- Data Confidentiality and Integrity: TLS encryption ensures traffic cannot be intercepted or modified in transit.
- Compliance: These measures contribute to meeting industry security standards (e.g., PCI DSS, HIPAA).
Q.28 What is a Kubernetes ConfigMap, and how do you use it?
A Kubernetes ConfigMap is a key-value store for holding non-confidential configuration data. It decouples configuration from pod definitions, making applications more portable and easily manageable.
Use Cases:
- Environment Variables: Provide application environment variables at runtime (e.g., database connection strings, API keys).
- External Configuration Files: Store files (e.g., XML, JSON) to be consumed by the application.
- Feature Flags: Manage feature toggles without redeploying pods.
Example:
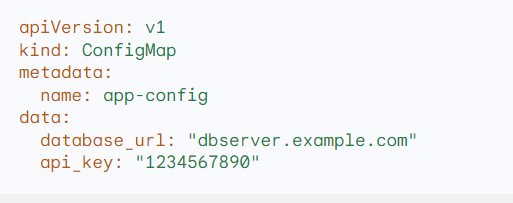
Q.29 Discuss the benefits of using Helm for managing Kubernetes applications.
Helm, the Kubernetes package manager, streamlines the installation, configuration, upgrade, and rollback of complex Kubernetes applications.
Use Cases:
- Templating: Helm charts use templates to simplify repeated Kubernetes manifests, making them easier to manage and update.
- Versioning and Rollbacks: Track application versions and easily roll back to previous releases if needed.
- Dependency Management: Manage dependencies between chart components for complex applications.
- Sharing and Reusability: Helm repositories make it easy to share and reuse charts.
Q.30 How do you monitor and visualize Kubernetes cluster health?
Robust monitoring and visualization are crucial for maintaining Kubernetes cluster health. Here’s how:
Use Cases:
- Metrics Collection: Tools like Prometheus gather metrics on resource usage, pod status, and application performance.
- Visualization: Dashboards built with tools like Grafana provide clear visualization of cluster health indicators and historical trends.
- Alerting: Configure alerts (e.g., with Prometheus Alertmanager) to trigger notifications based on pre-defined thresholds, enabling proactive issue resolution.
Part 1- Kubernetes Interview Q & A (Q1-Q5)
Part 2- Kubernetes Interview Q & A (Q6-Q10)
Part 3 – Kubernetes Interview Questions & Answers (Q.11 to Q.15)
Part 4 – Kubernetes Interview Questions & Answers (Q.16 to Q.20)
Part 5 – Kubernetes Interview Questions & Answers (Q.21 to Q.25)
Hope you find this post helpful.
Telegram: https://t.me/LearnDevOpsForFree
Twitter: https://twitter.com/techyoutbe
Youtube: https://www.youtube.com/@T3Ptech