Network Policies are a Kubernetes resource (API object) that define rules to control network traffic flow between pods within your cluster. They act like firewall rules specifically designed for Kubernetes environments.
Purpose of Kubernetes Network Policies:
- Micro-Segmentation: Isolate pods to limit potential attack spread and protect sensitive workloads.
- Controlled Communication: Define which pods are allowed to communicate with each other, improving security and compliance.
- Multi-tenant Authorization: Manage network access in multi-tenant clusters.
- Network Traffic Control: Enforce more granular network restrictions beyond simple “allow all” scenarios.
Key Concepts:
- Pods and Namespaces: Network Policies are applied to specific pods selected by labels, and often organized within namespaces.
- Policy Types:
- Ingress: Rules for incoming traffic to selected pods.
- Egress: Rules for outgoing traffic from selected pods.
- Selectors: Match labels are used to identify pods to which a policy applies.
- Traffic Specification: Can define allowed traffic based on:
- Pods: Selected by label
- Namespaces: Within the same or other namespaces
- IP Blocks: Using CIDR ranges
Workflow:
- Requirement Assessment: Identify communication patterns between pods and services.
- Policy Creation: Write Network Policy YAML files defining pod selectors, allowed traffic protocols, and source/destination selectors.
- Applying Policy: Use
kubectl apply -f policy.yamlto apply the policy to the cluster. - Enforcement: A compatible network plugin (like Calico or Cilium) enforces these rules.
Example (Simple Policy):
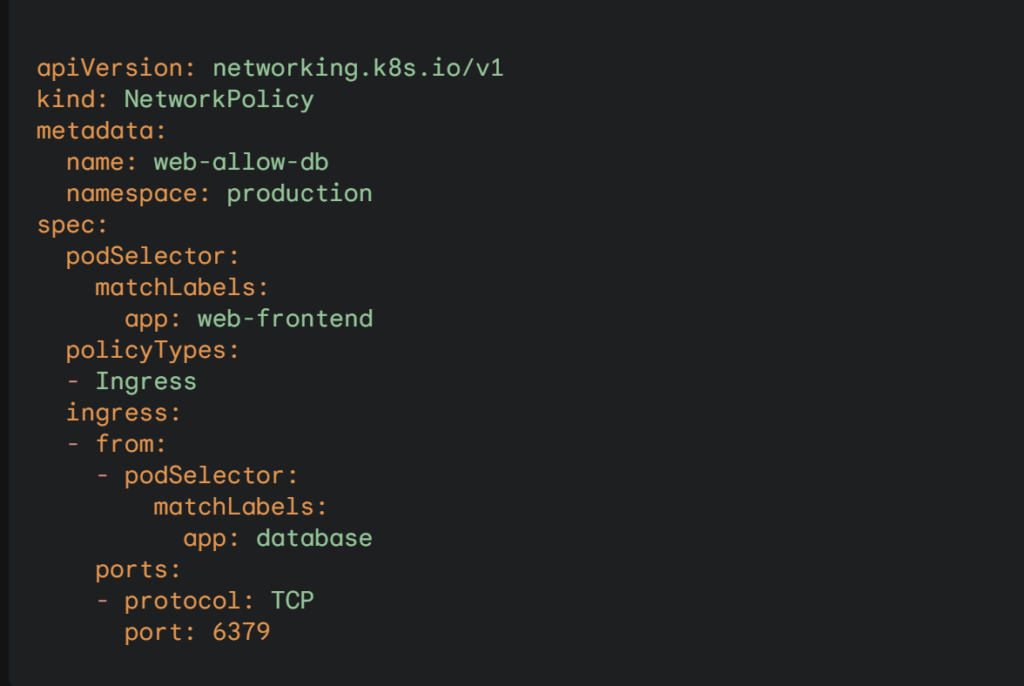
Important Notes:
Network Policies work at the IP level (Layer 3 and Layer 4).
Free Courses : Microsoft Azure (Concepts + Hands-on)